The digital minefield: Kaspersky experts share what’s new on the cyberthreat agenda in META

During Kaspersky’s 8th annual Cyber Security Weekend – META 2023, held in Almaty, Kazakhstan, the company’s experts discussed the biggest cyberthreats specifically targeting governments, enterprises, businesses and industrial organizations, while forecasting the trends that will influence the cybersecurity landscape in the future. The impact of Artificial Intelligence, compromised corporate data on the Darknet, risks carried by deepfakes as well as critical industry-specific threats – all these topics were discussed during the conference. Special attention was put on Kaspersky’s Cyber Immunity approach as a way to create solutions that are virtually impossible to compromise and that minimize the number of potential vulnerabilities.
A gradual rise in phishing attacks
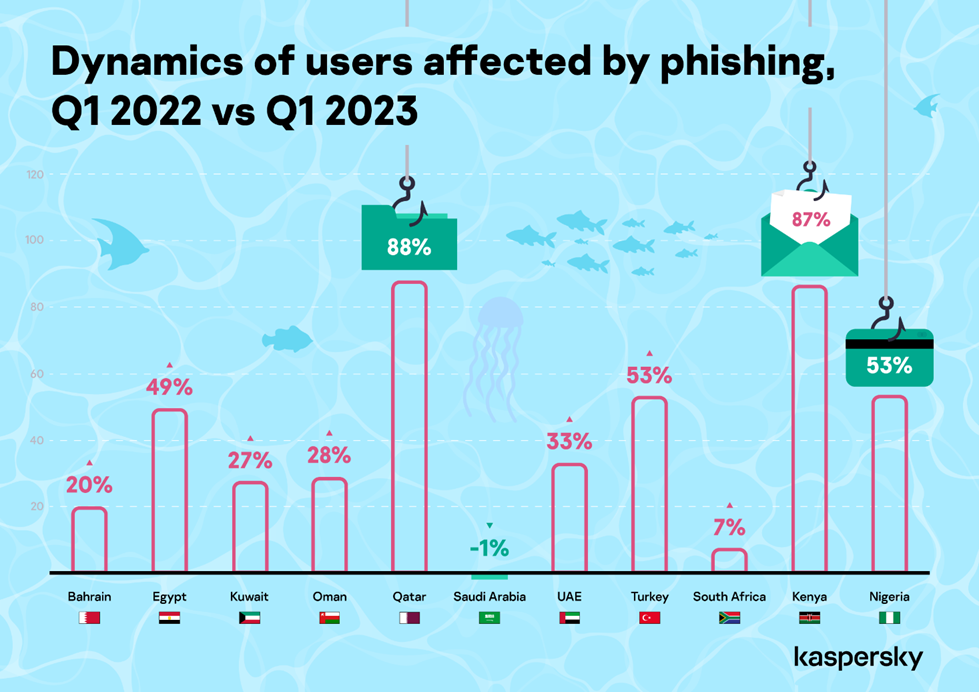
Diving deeper into social engineering cyberattacks, Kaspersky shared insights on phishing attacks which are most common in the META region. Comparing Q1 2022 to Q1 of 2023, Egypt (49%), UAE (33%), Qatar (88%), Oman (28%), Kuwait (27%) and Bahrain (20%) saw an increase in phishing attacks on users. On the other hand, phishing attacks in Saudi Arabia saw a slight decrease of 1% in Q1 of 2023 as compared to the same time period in 2022.
In the African region, phishing attacks grew in South Africa (7%), Nigeria (53%) and Kenya (87%) in Q1 of 2023 as compared to Q1 of 2022. Turkey (53%) witnessed an 53% increase in Q1 of 2023 as opposed to Q1 2022.
Ransomware
According to Kaspersky’s data, the number of organizations that faced ransomware mainly dropped in Q1 2023 in META region in comparison with the same period in 2022. The decline was observed in the Middle East region, where the number of B2B ransomware detections dropped by 61%. Over the same period ransomware attacks also dropped in Turkey, with a 59% decrease, as well as in Africa (a 65% drop).
“While we see a decrease in ransomware in the META region, that doesn’t mean that it becomes less dangerous. We can clearly see a distinctive trend in ransomware getting more sophisticated and targeted, exposing victims to more threats. In the recent years, ransomware groups have come a long way from being scattered gangs to businesses with distinctive traits of full-fledged industry. They continue to evolve by adopting techniques, such as developing cross-platform ransomware, embedding self-propagation capabilities and even using zero-day vulnerabilities that were previously affordable only for APT actors. It explains why it remains one of the most crucial threats for business despite the detection numbers decreasing”, comments Dmitry Galov, Senior Security Researcher at Kaspersky. “This is a global trend, while in those regions that put more efforts into proper protection measures on governmental and organizational levels the decrease is more dramatic. For countries with a lower level of cyber readiness ransomware remains a critical threat and the decrease is less prominent.”
Fast paced growth of trojan banking
New malware families and cyberattack campaigns have contributed to a rampant rise of Trojan banking attacks in Q1 of 2023 as compared to Q1 of 2022. The highest increase was in Turkey (238%). Overall, the Middle East too saw an increase in trojan banking attacks in the first quarter of 2023 – Kuwait (218%), Egypt (186%), Saudi Arabia (168%), Oman (115%), Qatar (99%), UAE (67%) and Bahrain (33%). Nigeria (268%) and Kenya (129%) also posted an increase.
Anticipated trends that will impact the cybersecurity landscape in META
Major drivers of growth in cybercrime are expected to be Crimeware and Advanced Persistent Threats (APTs).
Middle East to witness a rise in Crimeware: Crimeware is malicious software that is covertly installed on computers. Crimeware programs can be Trojans, keyloggers or spyware, and represent a new type of threat to security, posing new challenges and vulnerabilities. For example, some trojans are used to log every key you type (keyloggers), some capture screenshots when you are using banking websites, some download other malicious code, and others let a remote hacker access your system. What they each have in common is the ability to ‘steal’ your confidential information – such as passwords and PINs – and send it directly to the criminal. Armed with this information, the cybercriminal is then able to steal your money. Notably, North and South Africa too will evolve into a hotbed for Crimeware.
APT attacks in Central and East Africa: As countries in Central and East Africa accelerate on their digitization agenda, government and diplomatic institutions as well as key industrial organizations can become rich targets for stealthy APT attacks this year, according to Kaspersky experts. A strong cyber defense and intelligence sharing is important in this environment to identify and expose APT patterns, disarming cybercriminals and disrupting the kill chain.
Geographical expansion of APTs: Kaspersky experts have also witnessed advanced actors performing attacks with a focus on Europe, the US, the Middle East, and various parts of Asia. While most actors previously targeted victims in specific countries, more and more APTs are now targeting victims globally. For instance, MuddyWater, an actor that previously showed a preference for targeting Middle Eastern and North African entities, has expanded its malicious activity to organizations in Azerbaijan, Armenia, Malaysia, and Canada.




