Intensified scamming activity detected amid launch of the most popular smartphone
Apple held an event yesterday, and, where it introduced its new iPhone 13 lineup as well as the newest Apple Watch and AirPods versions. As year-to-year shows, not only Apple fans are interested in such events, but also scammers. For several years now, Kaspersky experts detect intensified scamming activities amid the long-awaited Apple presentations.
To learn more about how fraudsters monetize users’ interest in new Apple devices, Kaspersky researchers analyzed numerous phishing pages offering to buy the new version of iPhone as well as previous lines of bestselling AirPods and Apple Watch.
Most of these sites are fake pages offering to buy devices at a special price. Happy to find a good deal, a user sends money to fraudsters and, unsurprisingly, never receives the new pair of purchased headphones.

An example of phishing page offering to buy AirPods
There are also phishing pages providing users an exclusive opportunity to buy new iPhone before the official release. To place an order, users send their identifying information into untrustworthy hands. After that scammers may start using such data for bad purposes or sell it in the Dark Web. This fraud scheme is quite popular and, in some cases, scammers ask to pay for delivery fee – so users end up with not only sharing their personal data but also losing money. No need to say, the TV never gets to the deceived user.

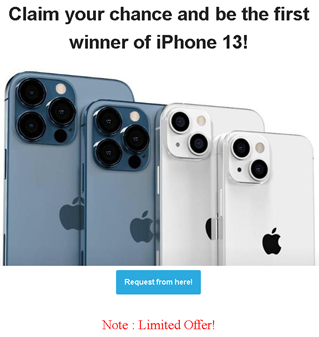
An example of phishing page offering to win iPhone 13
“Apple presentations have always been a popular lure for scammers to roll out malicious activity. For several years now, we see how fraudsters use the buzz around new iPhone release and start spreading malicious features. This only shows that scammers would happily benefit from anything that attracts users’ attention,” comments Tatyana Shcherbakova, security expert at Kaspersky.
In order to avoid falling victim to a scam, Kaspersky also advises users:
To be skeptical about any news or extremely generous offers and promotions
To verify that messages are coming from reliable sources
Not to follow links from suspicious emails or messages in instant messengers and social networks
To check the authenticity of websites they visit
To install a security solution with up-to-date databases that include knowledge of the latest phishing and spam resources





