Veracode Reveals Critical Security Debt Can Be Reduced by 75% With Speed of Remediation
- More Than 70% of Organizations Grapple with Security Debt and Nearly 50% Face “Critical” Debt
- State of Software Security 2024 Exposes Third-party Code as Major Culprit, with Two Thirds of Critical Debt Originating From Open-source Libraries
- Fixing Third-party Flaws Takes 50% Longer, But the Fastest-acting Development Teams Can Slash Critical Security Debt by 4x
BURLINGTON, Mass.–(BUSINESS WIRE /AETOSWire)– Veracode, a global leader in intelligent software security, today unveils its annual State of Software Security (SoSS) 2024 report, shedding light on the pressing issue of security debt in applications. Security debt, defined for this report as flaws that remain unfixed for longer than a year, exists in 42 percent of applications and 71 percent of organizations. Worryingly, 46 percent of organizations have persistent, high-severity flaws that constitute ‘critical’ security debt, putting businesses at serious risk in terms of impact on confidentiality, integrity, and availability.
According to the report, approximately 63 percent of applications have flaws in first-party code, while 70 percent contain flaws in third-party code imported via third-party libraries. This highlights the importance of testing both types throughout the software development life cycle. Remediation rates also vary by flaw type—fixing third-party flaws takes 50 percent longer, with half the known flaws fixed after 11 months, compared to seven months for first-party flaws.
There is good news, however: high-severity security flaws in applications have decreased by half since 2016, indicating progress in software security practices and that speed of remediation has a material impact on critical security debt.
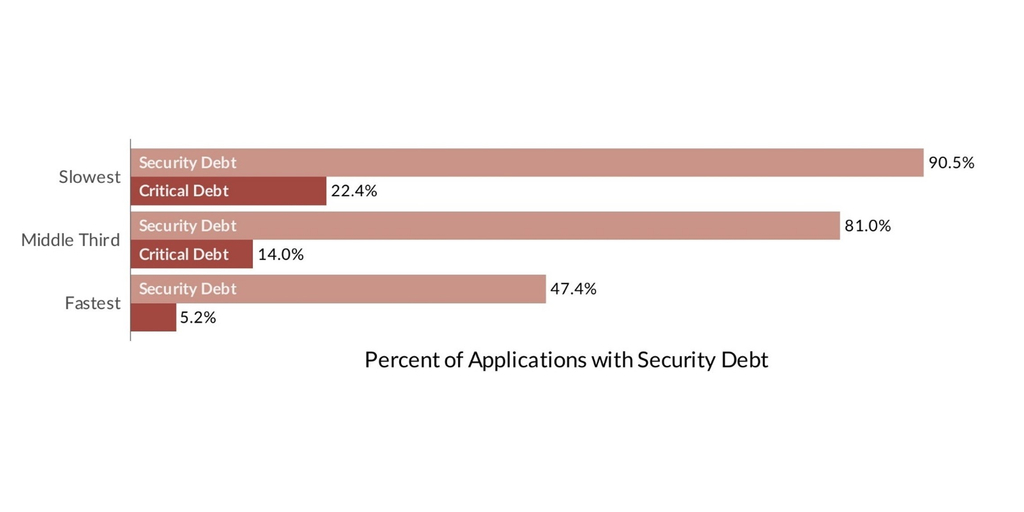
SoSS 2024 reveals development teams that fix flaws the fastest reduce critical security debt by 75 percent—from 22.4 percent of applications to just over five percent. Moreover, these fast-acting teams are four times less likely to let critical security debt materialize in their applications in the first place.
Chris Eng, Chief Research Officer at Veracode, said, “While we continue to see improvements in the security landscape, these findings are a wake-up call for organizations to address their security debt head-on. By prioritizing flaw remediation, focusing on third-party code security, and adopting efficient development practices, organizations can significantly reduce their security debt and enhance the overall state of software security across the board.”
Addressing AI and the Software Supply Chain
In an era where AI (artificial intelligence) is rapidly revolutionizing software development, the report highlights a concerning trend. Chris said, “Despite the speed and efficiency AI brings to software development, it does not necessarily produce code that’s secure. Research has shown that 36 percent of code generated by GitHub CoPilot contains security flaws.” This proliferation of insecure code at scale poses a significant risk to organizations and the software supply chain, leading to the accumulation of security debt over time.
Risk Prioritization is Key
Veracode’s research also found remediation capacity among teams to be constrained, with only 64 percent of applications having a remediation capacity that’s sufficient to eliminate critical security debt. In fact, only two out of ten applications show an average monthly fix rate that exceeds ten percent of all security flaws. This suggests, even in cases where teams’ fix capacity is sufficient, they are not prioritizing critical flaws.
Despite this, there is hope for success. Only three percent of all flaws constitute critical security debt, and this subset represents the largest risk exposure for applications. By prioritizing that three percent, organizations can achieve maximum risk reduction with focused effort.
Chris closed, “AI also paves the way for a new frontier in software security by empowering organizations to scale remediation efforts and more easily address the long backlog of security debt, as well as new flaws that emerge. The vast majority of CWEs (Common Weakness Enumeration) with a severity rating from medium to very high can be addressed through AI-generated code edits from Veracode Fix.”
The full State of Software Security 2024 report is available to download on the Veracode website. To access the report and gain deeper insights into the findings and recommendations, visit the website. A blog outlining the key findings from the report is also available to read.




