Hot or cold? Kaspersky uncovers new phishing scheme targeting cryptocurrency users worldwide

Kaspersky has unearthed a phishing campaign targeting cryptocurrency users across the globe. The scheme showcases the ever-evolving tactics used by cybercriminals, reflecting cryptocurrency’s increasing appeal. During the spring of 2023 alone, Kaspersky’s solutions detected and thwarted over 85,000 scam emails, encompassing both hot and cold wallets. Kaspersky provides an in-depth report revealing the intricacies of these two distinct email attack techniques and enlightening the differences in hot and cold cryptocurrency storage methods.
With over 400,000,000 cryptocurrency wallet owners globally, as reported by Crypto.com, the spike in popularity of hot wallets comes from their accessible nature. Online storage services such as crypto exchanges and dedicated apps have become prime targets for cybercriminals due to their constant internet connectivity.
Phishing attacks aimed at hot wallet users typically employ relatively simple tactics, often exploiting non-technical individuals. Malicious actors impersonate well-known crypto exchanges through fraudulent emails, urging users to validate transactions or reconfirm the security of their wallets. Unsuspecting victims who click on the links are redirected to fake web pages that prompt them to enter their seed phrase — an essential element for wallet recovery. By gaining access to the seed phrase, scammers can seize control of the victim’s wallet and transfer funds to their own accounts.
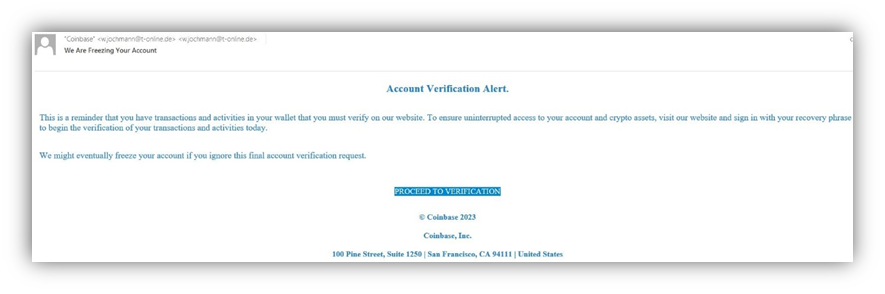
Example of a phishing email targeting Coinbase users
In contrast, cold wallets are entirely offline storage systems, like a dedicated device or even a private key jotted down on paper. Hardware wallets are a prevalent type of cold wallet. They have garnered favor among users storing substantial cryptocurrency holdings due to their enhanced security measures. However, Kaspersky researchers recently discovered a targeted phishing campaign specifically tailored to exploit cold wallet owners. This campaign is initiated with an email masquerading as a prominent cryptocurrency exchange, Ripple, enticing recipients with the promise of participating in an XRP token giveaway.
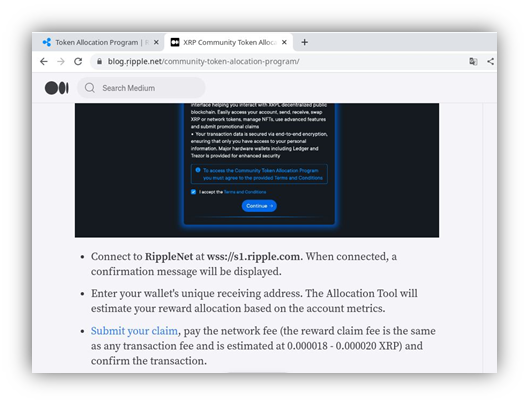
Example of a fake Ripple blog
Instead of directing victims to a phishing page, scammers employ a more sophisticated technique by creating a deceptive blog post that mimics the Ripple website’s design.
This blog offers users the chance to enter a giveaway of XRP tokens, the platform’s internal cryptocurrency, by following specified link. After following the link to a fake Ripple page using a domain name that closely resembles the official Ripple domain (a Punycode phishing attack), victims are prompted to connect their hardware wallets, such as Trezor or Ledger, to the scam website. This interaction allows scammers to gain access to victims’ accounts and initiate fraudulent transactions.
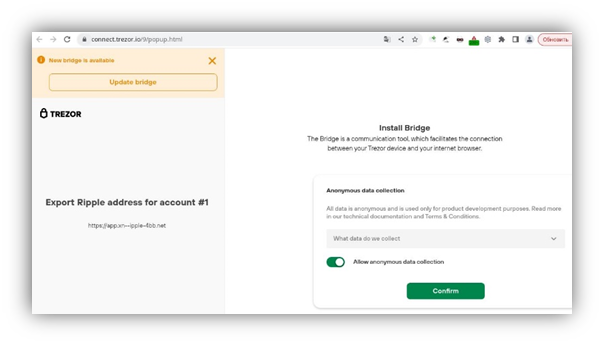
Trezor Connect: confirming the connection to the scam site
As of spring 2023, Kaspersky’s antispam solutions successfully detected and blocked over 85,000 scam emails aimed at cryptocurrency users. This nefarious campaign reached its peak in March, with more than 34,000 intercepted malicious messages. Kaspersky continued safeguarding cryptocurrency users in April and May, thwarting roughly 19,902 and 30,816 scam emails in these months, respectively.
“We are witnessing an ongoing surge in the popularity of cryptocurrencies, and with it, the need for users to stay alert and implement strong security measures to protect their digital assets. It is crucial to verify the authenticity of the sender and exercise caution before clicking on any links or providing sensitive information,” comments Roman Dedenok, a security expert at Kaspersky.
Read the full report on the cryptophishing campaign at Securelist.com.
To keep crypto assets safe, Kaspersky experts also recommend the following:
Purchase from official sources: Only buy hardware wallets from official and trusted sources, such as the manufacturer’s website or authorized resellers.
Inspect your wallet: Scan your new hardware wallet for any signs of tampering before using it.
Verify the firmware: Always verify that the firmware on the hardware wallet is legitimate and up to date. This can be done by checking the manufacturer’s website for the latest version.
Secure your seed phrase: When setting up your hardware wallet, make sure to write down and securely store your seed phrase. A reliable security solution, such as Kaspersky Premium, will protect your crypto details stored on your mobile device or PC.
Use a strong password: If your hardware wallet allows for a password, opt for a strong and unique one. Avoid using easily guessable passwords or reusing passwords from other accounts. To manage passwords effectively and securely, consider utilizing Kaspersky Password Manager.




