Fortinet Warns of AI-Powered Attacks as Automated Scans Hit 36,000 Per Second
500% Spike in Data Leaks as Infostealer Malware Floods Underground Forums
Global report highlights rising risks for enterprises as cybercriminals scale attacks using generative AI and underground tools
Fortinet® (NASDAQ: FTNT), the global cybersecurity leader driving the convergence of networking and security, has released its 2025 Global Threat Landscape Report, revealing a dramatic surge in cyber threats across 2024 driven by the rapid adoption of artificial intelligence, automation, and commoditized hacking tools. According to the report, these developments have significantly eroded the effectiveness of traditional security defenses and accelerated the pace and scale of attacks.
Compiled by FortiGuard Labs, the report outlines a sharp 16.7% year-over-year increase in automated scanning activity, with a staggering 36,000 scans per second recorded globally. attackers are increasingly “shifting left,” targeting vulnerable digital assets earlier in the attack lifecycle, particularly protocols such as SIP(Session Initiation Protocol), RDP (Remote Desktop Protocol), and operational technologies (OT) and Internet of Things (IoT) systems like Modbus TCP.
Cybercrime Marketplace Expands with Record Vulnerabilities
The dark web has evolved into a mature ecosystem for exploit kits and corporate access data. In 2024, more than 40,000 new vulnerabilities were added to the U.S. National Vulnerability Database, a 39% rise from 2023. Threat actors capitalized on this surge by selling initial access packages, often bundled with enterprise credentials (20%), RDP access (19%), admin panels (13%), and malicious web shells (12%).
Infostealers Drive Record Credential Leaks
One of the most alarming trends identified in the report is the exponential growth of data leaks through infostealer malware. FortiGuard Labs noted a 500% increase in available logs from compromised systems, with over 1.7 billion stolen credentials circulating on underground forums in 2024 alone. This flood of stolen data has led to a sharp increase in targeted cyberattacks against businesses and individuals.
AI-Powered Phishing, Sectoral Targeting Rise
Fortinet also flagged the increasing use of generative AI tools—such as FraudGPT, BlackmailerV3, and ElevenLabs—by cybercriminals to craft sophisticated phishing campaigns and evade traditional detection mechanisms. These tools are enabling attackers to create highly convincing content at scale, significantly raising the threat level.
Meanwhile, manufacturing emerged as the most targeted sector (17%), followed by business services (11%), construction (9%), and retail (9%). Attackers used tailored exploitation strategies—often backed by nation-state actors or Ransomware-as-a-Service (RaaS) groups—to maximize impact. Geographically, the United States faced 61% of all documented attacks, far surpassing the UK (6%) and Canada (5%).
Cloud and Identity Risks Remain Critical
The report highlights ongoing vulnerabilities in cloud environments, driven by exposed storage, misconfigured services, and over-permissioned identities. In 70% of the cloud incidents analyzed, threat actors gained access through anomalous login locations, underscoring the need for advanced identity monitoring and adaptive access controls.
In a disturbing development, over 100 billion compromised records were shared across darknet forums in 2024—a 42% increase over the previous year. This surge was largely powered by “combo lists,” which bundle stolen usernames, passwords, and emails for use in automated credential-stuffing attacks. Cybercrime groups such as BestCombo, BloddyMery, and ValidMail were among the most prolific actors.
Call for a Strategic Shift in Cyber Defense
“Our 2025 Global Threat Landscape Report makes it clear: cybercriminals are scaling faster than ever, using AI and automation to gain the upper hand,” said Derek Manky, Chief Security Strategist and Global Vice President of Threat Intelligence at FortiGuard Labs. “Defenders must abandon outdated security playbooks and transition to proactive, intelligence-driven strategies that incorporate AI, zero trust architectures, and continuous threat exposure management.”
Actionable Guidance for CISOs
Fortinet’s report features a “CISO Playbook for Adversary Defense, offering strategic recommendations for IT leaders, including:
- Continuous Threat Exposure Management (CTEM): Real-time attack surface monitoring and automated response.
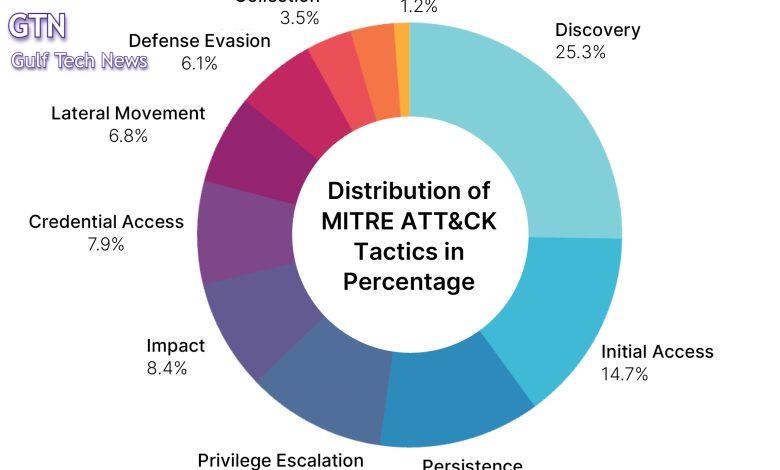
- Real-World Attack Simulations: Red/purple teaming and MITRE ATT&CK-based testing against real-world threats.
- Attack Surface Reduction: Use of ASM tools to uncover vulnerable assets and leaked credentials.
- Risk-Based Patch Management: Prioritization using EPSS, CVSS scores, and threat actor telemetry.
- Dark Web Intelligence Integration: Monitoring for emerging ransomware threats and hacktivist campaigns.
With cybercriminals rapidly weaponizing emerging technologies, Fortinet urges organizations to adopt a more resilient, intelligence-led approach to cybersecurity.